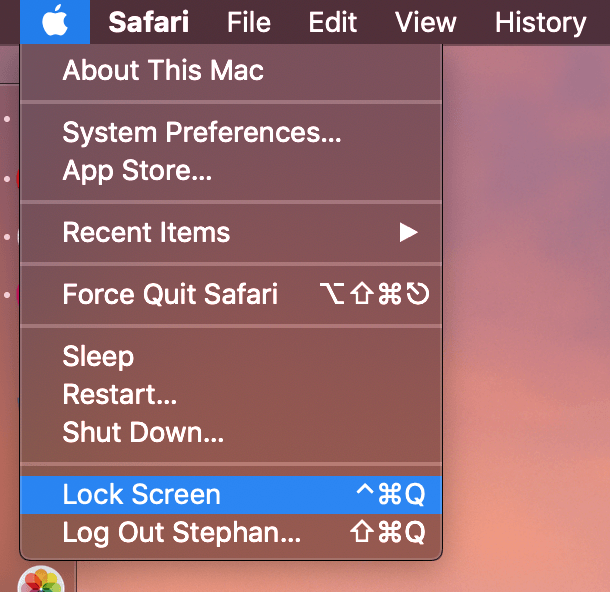
How to quickly secure a macOS system? A streamlined approach to system security.
A key aspect of safeguarding macOS systems involves methods for rapidly locking the screen. This encompasses various techniques, including keyboard shortcuts, mouse clicks, and potentially specific system preferences. These methods allow users to temporarily disable screen access without explictly logging out or shutting down. For example, pressing Command + Control + Q often acts as an immediate screen lock. Other solutions might involve activating a built-in feature that triggers a visual lock or prompt requiring a password to regain access. The effectiveness of the approach depends on the specific macOS version and its built-in functionalities.
Security is paramount in modern digital environments. Prompt screen locking prevents unauthorized access to sensitive information, even during brief unattended periods. This is especially important in shared or public spaces where safeguarding confidential documents and data is critical. The immediate nature of such shortcuts enhances the overall security posture of the device. Efficiency in this process is a benefit for users juggling multiple tasks or moving between applications, ensuring quick and seamless transition between work sessions.
This section will now delve deeper into the technical aspects of screen lock mechanisms, focusing on their implementation and the security considerations.
macOS Lock Shortcut
Effective screen locking on macOS is crucial for security and productivity. Proper utilization of shortcuts streamlines the process. These shortcuts protect sensitive data and maintain workflow efficiency.
- Security
- Efficiency
- Accessibility
- Keyboard
- Password protection
- System settings
- Functionality
Security relies on swift and reliable locking mechanisms. Efficiency is enhanced when locking requires minimal steps. Accessibility ensures usability for all users, regardless of experience level. Keyboard shortcuts provide quick and convenient access. Password protection maintains data confidentiality. System settings dictate the procedures for configuring lock shortcuts. Functionality encompasses the full range of screen lock capabilities, from locking to unlocking. For instance, a combination of Command-Control-Q can rapidly lock the screen. Well-designed shortcuts lead to a cohesive system, improving the overall user experience by simplifying security measures.
1. Security
Security is fundamental to macOS. A robust system relies on mechanisms that protect sensitive data from unauthorized access. macOS lock shortcuts are a critical component of this security infrastructure. Their function is to swiftly and reliably restrict access to the system, preventing data breaches and misuse. A compromised system exposes confidential information and potentially jeopardizes user accounts and personal data. Effective locking mechanisms form an immediate defense against such threats, acting as a first line of defense. For instance, a misplaced device or a temporary unattended situation necessitates rapid security protocols to prevent unauthorized access.
The practical significance of understanding this connection is evident in numerous scenarios. Imagine a shared computer in a public space. Without a secure locking mechanism, sensitive data and files could be vulnerable to unwanted access. A reliable shortcut for locking the screen quickly prevents this. Furthermore, in a home environment, a lock shortcut allows users to temporarily secure their system when stepping away, safeguarding personal or financial data from prying eyes. Similarly, in professional settings, the protection of confidential business information depends directly on the efficacy of these lock features. Swift implementation minimizes the risk associated with potential lapses in attention or sudden interruptions. Consequently, understanding the role of lock shortcuts in security fosters a culture of responsible digital citizenship.
In conclusion, macOS lock shortcuts are integral to the overall security posture of the system. Their primary function is to swiftly impede unauthorized access. This protective mechanism is paramount in various real-world scenarios, emphasizing the critical importance of secure data practices. By understanding the connection between security and these shortcuts, users can proactively mitigate the risk of data breaches and misuse. This understanding translates into responsible digital habits and ensures a safer and more secure online environment.
2. Efficiency
Efficient use of macOS lock shortcuts directly impacts productivity and user experience. Swift access to security measures reduces interruptions and maintains workflow continuity. The speed and ease of locking the screen are critical aspects of a well-designed user interface, impacting overall system responsiveness and preventing unauthorized access during brief interruptions.
- Minimized Interruptions
Rapid locking procedures minimize interruptions to user tasks. Shortcuts allow users to quickly secure the system during brief absences or transitions. This immediate action prevents accidental access and ensures that sensitive information remains confidential during temporary unattended periods. This is especially relevant in shared environments or when working with sensitive data, maintaining a secure and focused workflow.
- Enhanced Workflow Continuity
By swiftly locking the screen, interruptions are mitigated, ensuring that work sessions are not disrupted during temporary lapses. This streamlined procedure protects sensitive information while allowing for seamless transitions between tasks. Efficient access to locking mechanisms maintains workflow continuity, particularly useful for users multitasking or moving between applications.
- Increased System Responsiveness
A system that allows for quick locking and unlocking contributes to a more responsive user experience. This is especially apparent when compared with systems that require more complex steps to secure the system. By enabling fast security measures, macOS facilitates a streamlined user environment. Reduced delay times in the locking process contribute to a positive user experience, preventing frustration due to system sluggishness.
- Improved Productivity
The combination of efficiency and security enhances productivity. Rapid locking procedures allow for secure transitions between tasks and prevent interruptions during work sessions. Users can confidently step away from the system without concern for data breaches or misuse, leading to focused work sessions and increased productivity. The smooth implementation of these processes reduces wasted time and potential security risks.
In summary, macOS lock shortcuts' efficiency manifests in reduced interruptions, enhanced workflow continuity, increased system responsiveness, and ultimately, improved user productivity. Effective use of these tools directly contributes to a positive user experience, fostering a secure and efficient computing environment.
3. Accessibility
Accessibility in the context of macOS lock shortcuts necessitates consideration of diverse user needs and abilities. Effective shortcuts must be usable by individuals with varying levels of technical proficiency and physical limitations. This inclusivity ensures the security features are readily available to a broad spectrum of users.
- Keyboard Focus and Navigation
macOS lock shortcuts relying on keyboard commands must be easily navigable for users employing assistive technologies like screen readers. Clear and consistent keybindings enable users to initiate the locking process without hindering their existing workflows or requiring mouse interaction. The system should prioritize intuitive keyboard navigation throughout the security process. This is especially critical for users who primarily interact with the system through keyboard inputs, or for those with limited or no mouse access.
- Customization Options
Recognizing individual preferences, customization options allow users to tailor locking procedures to their specific requirements. This might include configurable shortcut keys, adjustable time-outs, and different lock screens depending on user roles and security levels. Such adaptability is crucial for accommodating diverse needs and work styles while ensuring a smooth and efficient user experience. A range of customizable settings is essential to facilitate personalized security practices. For instance, users with visual impairments may require alternative indicators for locking status.
- Clear Visual Cues
Visual cues are equally important for users who may not exclusively rely on auditory feedback. The system should provide readily apparent visual indicators confirming the successful execution of the lock shortcut, preventing ambiguities and enhancing user experience. These visual cues should be prominent and easily distinguishable across varying screen displays or configurations. Clear and immediate visual confirmation of lock initiation assures the user the action has been completed successfully.
- Error Handling and Feedback
Effective error handling is vital for seamless user experience. The system must provide clear and concise feedback in the event of incorrect input or unsuccessful shortcut executions. Proper error handling informs the user without confusion, ensuring they understand the issue and can resolve it readily. For example, an informative message might provide feedback on the incorrect shortcut key combination. This feature significantly enhances accessibility for all users, reducing frustration and promoting the effective implementation of these security protocols.
In essence, accessibility in macOS lock shortcuts hinges on a combination of navigable keybindings, customizable preferences, clear visual cues, and robust error feedback mechanisms. By addressing these crucial considerations, the system ensures that security protocols are accessible to all users, fostering inclusivity and streamlining overall user interaction with the platform. This, in turn, enhances the usability and overall security posture of the system.
4. Keyboard
The keyboard is a fundamental input device for macOS, playing a critical role in the implementation of lock shortcuts. Its direct interaction with the operating system facilitates quick and secure access to these functions. Efficient keyboard-based shortcuts significantly enhance system security and usability.
- Direct Control and Speed
Keyboard shortcuts offer immediate control over system functions. The speed at which these shortcuts execute commands allows rapid screen locking, enhancing system responsiveness and security in dynamic situations. Direct input minimizes user interaction steps, fostering a streamlined workflow, particularly when combined with time-sensitive operations or temporary unattended use.
- Accessibility and Configurability
Keybindings can be configured to accommodate diverse user needs and preferences. Accessibility features allow customizable key combinations for users with varying technical proficiency or physical limitations. This adaptability ensures usability across diverse user groups and fosters a secure, inclusive environment. Customization options may include the ability to assign keyboard shortcuts to specific programs or functions.
- Security and Confidentiality
Keyboard shortcuts are integral to maintaining system security. The discrete nature of keystrokes enhances confidentiality, preventing accidental or unauthorized activation of locking procedures. The unique character combinations employed in lock shortcuts protect sensitive data during periods of user inactivity. The secure nature of keyboard input also minimizes the risk of accidental or malicious activation of screen lock functions.
- Integration with System Architecture
The keyboard's integration into the macOS operating system is essential for lock shortcut functionality. The operating system recognizes and interprets keystrokes, enabling seamless activation of security protocols. This integration ensures seamless communication between the input device and the system, allowing for efficient execution of locking procedures. Keyboard shortcuts directly interact with the system's core functionalities, contributing to their efficacy and reliability.
In conclusion, the keyboard's role in macOS lock shortcuts is multifaceted, encompassing speed, accessibility, security, and seamless integration. Keyboard-based shortcuts represent a crucial element in user-friendly and reliable security protocols within the macOS ecosystem.
5. Password protection
Password protection is inextricably linked to macOS lock shortcuts. The effectiveness of a lock shortcut relies fundamentally on a strong password. A secure password acts as the key that unlocks access to the system once locked. Without a valid password, attempts to bypass the locked screen will fail. This interdependence highlights the crucial role of robust password practices as a necessary component of effective security protocols. An ineffective password system undermines the security benefits of a robust lock shortcut mechanism.
The significance of strong password protection is underscored in numerous real-world scenarios. Imagine a user employing a complex lock shortcut but using a weak, easily guessed password. The security provided by the shortcut becomes considerably less effective, potentially exposing sensitive information. Conversely, a strong password combined with a lock shortcut provides a layered defense against unauthorized access. In professional contexts, the safeguarding of confidential company data depends on the rigorous combination of strong passwords and robust security protocols, including lock shortcuts. An effective security posture requires a comprehensive approach to protection, addressing both the methods of locking and the integrity of the passwords used for authentication. Consequently, understanding this interconnectedness is vital for achieving an optimal security posture.
In conclusion, password protection and macOS lock shortcuts are mutually reinforcing components of a comprehensive security strategy. A strong password is essential to ensure the effectiveness of lock shortcuts. This integration reflects a layered approach to security, where multiple safeguards are combined to provide maximum protection against unauthorized access. Ignoring either aspectrobust passwords or effective lock shortcutsweakens the overall security posture. Understanding this crucial connection is imperative for maintaining a secure and reliable digital environment, particularly in professional or sensitive contexts.
6. System Settings
System settings are fundamental to macOS lock shortcuts. Configuration within system settings dictates the available lock shortcut options, and consequently, the security posture of the system. The specific key combinations employed as shortcuts are often predefined within these settings. This pre-configuration ensures compatibility and consistent functionality across different macOS versions and configurations. System settings also govern additional features related to the lock mechanism, such as the duration of inactivity before the screen automatically locks, the types of visual cues that signal locking, and the appearance of the lock screen itself. Altering these settings within the system preferences section modifies the behavior of lock shortcuts, affecting security, accessibility, and user experience.
Practical examples illustrate this connection. A user might adjust system settings to require a password after a specific period of inactivity. This modification directly affects the efficacy of the lock shortcut, transforming it from a simple keyboard command to a mechanism that enforces user authentication. Similarly, altering visual cues associated with the locking processsuch as the appearance of a lock iconis a setting adjustment within the system. Such adjustments have a practical impact on the ease and reliability of the locking process. A poorly configured system settings environment can compromise the effectiveness of lock shortcuts, potentially leaving the system vulnerable. Conversely, carefully configured system settings enhance the security and usability of lock shortcuts by aligning them with user preferences and the prevailing security context. The user experience is directly correlated to these adjustments, highlighting the importance of configuring system settings appropriately.
In summary, system settings directly control the functionality and application of macOS lock shortcuts. Understanding this configuration process is paramount for maximizing the security and utility of these shortcuts. Properly configured system settings enable users to tailor lock shortcuts to their specific needs and security requirements. Conversely, misconfigurations can reduce the effectiveness of these shortcuts. This understanding fosters a proactive approach to system security, emphasizing the crucial link between user interaction with system settings and the overall security posture of the macOS environment. By addressing the underlying configurations, users and administrators can optimize the interplay between system settings and lock shortcuts, ensuring robust security and a seamless user experience.
7. Functionality
The functionality of macOS lock shortcuts encompasses the entire spectrum of their operational capabilities. A robust lock mechanism hinges on the seamless integration of its various components. This includes the ability to rapidly initiate the locking process, the reliable authentication process following the lock, and the assurance that sensitive information is effectively protected. The functionality of the shortcut extends to safeguarding against accidental access, a key aspect of maintaining security and data integrity. The interplay between the different components of the lock processthe shortcut itself, the subsequent authentication, and the protection mechanismscomprises the comprehensive functionality of this security feature. Examples include the seamless locking during unattended periods, ensuring data protection against casual access, or providing a fast locking option during sensitive operations.
Practical applications of understanding this functionality are numerous. For instance, in a shared workspace, quick locking prevents unauthorized access to sensitive documents. In a personal environment, a dependable locking mechanism protects against unwanted intrusion. In either case, efficient lock functionality assures that the system remains secure during periods of non-use, significantly mitigating the risk of data breaches. This is crucial for maintaining trust and protecting valuable information. Moreover, reliable functionality enhances the user experience. A predictable and quick locking mechanism contributes to user satisfaction and ease of use. Such a feature contributes to a more streamlined and secure workflow. Understanding the full spectrum of functionality ensures a secure and user-friendly computing experience.
In conclusion, the functionality of macOS lock shortcuts is more than just a series of steps; it's a comprehensive security mechanism. This intricate system of actions and reactions protects data and maintains system integrity. Its efficient execution demonstrates a well-designed security infrastructure, contributing significantly to the overall user experience. Recognizing this multifaceted functionality is essential for effective system management, reinforcing the importance of security protocols and ensuring safe data handling within the macOS environment. Understanding and appreciating this function enhances the user's overall security experience and provides a reliable method of data protection.
Frequently Asked Questions about macOS Lock Shortcuts
This section addresses common queries regarding macOS lock shortcuts, providing concise and informative answers to frequently encountered concerns.
Question 1: What are macOS lock shortcuts?
macOS lock shortcuts are predefined key combinations used to quickly lock the screen, temporarily restricting access to sensitive data and system resources. These shortcuts vary based on macOS version and configuration, but typically involve the Command key in conjunction with other modifier keys.
Question 2: Why use macOS lock shortcuts?
Employing macOS lock shortcuts enhances security by rapidly preventing unauthorized access to the system during brief periods of unattended use. This is particularly pertinent in shared or public environments, safeguarding sensitive data from potential breaches.
Question 3: How do I find macOS lock shortcuts?
Specific lock shortcuts may vary across macOS versions. Consulting the macOS user documentation, checking system preferences, or referring to online resources specific to the macOS version can identify the appropriate shortcuts for the system configuration.
Question 4: Are macOS lock shortcuts effective against sophisticated attacks?
While macOS lock shortcuts provide a fundamental level of security against casual access, they are not designed to counter sophisticated or targeted attacks. Stronger security measures, including robust passwords and appropriate access controls, are required for comprehensive protection against advanced threats.
Question 5: How can I customize macOS lock shortcuts?
Customization of macOS lock shortcuts is often not directly possible. The system settings typically dictate the predefined key combinations used for the screen locking process, rather than offering individual user configurations for these specific shortcuts.
In summary, macOS lock shortcuts are essential tools for rapid system security. Understanding their purpose, limitations, and configuration is crucial for responsible system use and the effective protection of data. Users should recognize the combined nature of security measures, including but not limited to appropriate passwords and other security protocols, for a robust security posture.
This concludes the FAQ section. The following sections will delve deeper into the technical aspects of macOS security.
Conclusion
This exploration of macOS lock shortcuts reveals a multifaceted security mechanism crucial for data protection and system integrity. The swiftness and reliability of these shortcuts contribute to a user-friendly yet secure environment. Key aspects highlighted include the importance of security in diverse contexts, the efficiency of streamlined processes, the accessibility considerations for varied user needs, the fundamental role of keyboard interaction, the criticality of strong passwords, the importance of system settings configuration, and the comprehensive functionality encompassing all aspects of the locking process. Understanding these interconnected elements is paramount for effective system management. Misconfigurations or inadequate implementation can compromise the system's overall security posture. Consequently, responsible system usage, emphasizing appropriate password practices and a well-configured environment, is indispensable for maximizing the effectiveness of these shortcuts.
In conclusion, macOS lock shortcuts are not merely convenience features; they are integral components of a robust security infrastructure. The continued advancement and refinement of security protocols are essential. Users are encouraged to familiarize themselves with the applicable system settings and associated security best practices. By comprehending these core principles, individuals and organizations can effectively mitigate risks, safeguarding critical information and promoting a secure digital environment. Continuous awareness and adaptation to evolving security threats are vital for maintaining a robust defense posture.
Article Recommendations
- How Did Aubreigh Wyatt Kill Herself
- The Uncovering Of Jelani Asar Snipes A Mystery Solved
- Is Keanu Reeves Sick